dimanche 21 décembre 2014
Montres Connectées
Montres Connectées
http://www.lemonde.fr/pixels/article/2014/12/18/on-a-teste-pour-vous-les-montres-connectees_4542553_4408996.html
mercredi 15 octobre 2014
Guerre des navigateurs
Web Standards Project
http://fr.wikipedia.org/wiki/Web_Standards_Project
Quelques tests
http://acid3.acidtests.org/
http://fr.wikipedia.org/wiki/Acid3
http://html5test.com/
mardi 20 mai 2014
AMAZONE AWS PRICING
Amazon S3 Pricing
Storage price
reference :
Standard Storage Reduced Redundancy Storage Glacier Storage
1 TB / month - $0.0240/GB up to $0.0300/GB (24$/30$/month)
BACKUP $0.0100 / GB
dimanche 2 février 2014
49152 CORES on 4U Server
They took this :
and replace-it by this :
TEGRA K1
192-core-Super Chip
SERVER CAN RUN 256 CPU AT 192 CORES = TOTAL OF 49152 CORES,
FOR 1 SINGLE SERVER. (2014)
mercredi 8 janvier 2014
ANDROiD | The Android Source Code
The Android Source Code
*** Build and run ANDROID(OS. Not Apps) on your phone. This step is at your risk. You can HANG your phone.
Source code
http://source.android.com/source
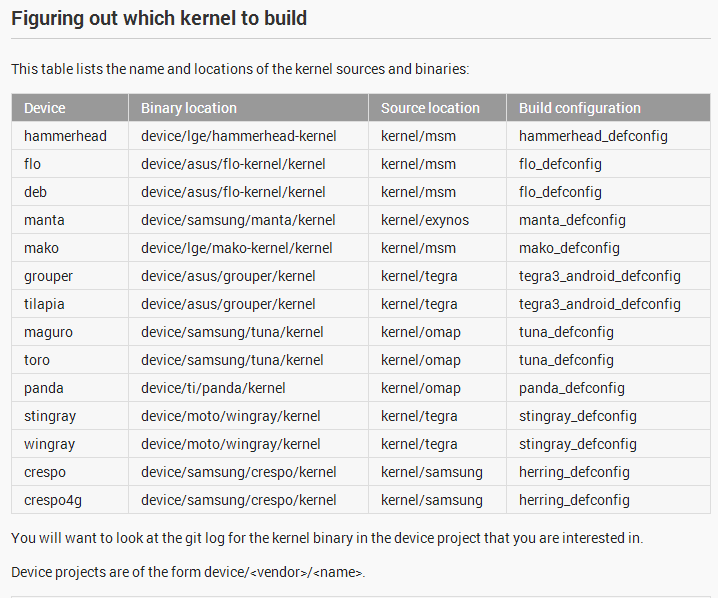
Kernel / ANDROID | Real headache >
Downloading and Building
http://source.android.com/source/building.html
*** Build and run ANDROID(OS. Not Apps) on your phone. This step is at your risk. You can HANG your phone.
Source code
http://source.android.com/source
Kernel / ANDROID | Real headache >
Downloading and Building
http://source.android.com/source/building.html
>>* What are the risks of rooting? SOURCE : Android Newbie’s Guide to Rooting
http://www.talkandroid.com/guides/beginner/newbies-guide-to-rooting/
http://www.talkandroid.com/guides/beginner/newbies-guide-to-rooting/
Okay, honestly this is what most of you want to know, right? I mean, if it were easy and there were no risks then everyone would be rooted. Aside from completely voiding your factory warranty, to be blunt, you can seriously mess up your phone – like to the point where you’ve made it into a glorified paperweight. That’s the big risk. I know, it’s a massive risk, but it’s kind of along those lines of a risk that has to be pointed out like all the risks that go along with taking medicine.
I mean, it’s a risk for me to drive to work each morning. It’s a risk to fly. I could go on and on. However, it’s more of a disclaimer than anything, and a heads up to BE CAREFUL. Additionally, once rooted with full control of your device, it opens your device up to the slim possibility of someone taking control over it like a hacker at a mall, bar, etc. However, there are measures to prevent this once a little research is done after you’re rooted.
Inscription à :
Articles (Atom)